How to successfully implement a contactless CPU card project
introduction
With the gradual promotion of non-contact IC card technology in China, non-contact applications have become more and more popular among people with their quick and convenient operation methods, and have gradually become the technology of choice for public transportation and urban card construction.
The non-contact IC card technology that was put into use in the early days was mostly a logical encryption card, such as the most famous Mifare 1 card of Philips (now NXP). The contactless logic encryption card technology has been quickly favored by users with its low cost, concise transaction process and simple system architecture, and has been rapidly applied and developed. According to incomplete statistics, as of the end of last year, the number of non-contact logic encryption cards in various fields in China has reached hundreds of millions.
With the continuous application of contactless logic encryption cards, the inadequacies of contactless logic encryption card technology are increasingly exposed, and it is difficult to meet the requirements of higher security and more complex multiple applications. Therefore, contactless CPU card technology is becoming a technically updated option.
First, the system architecture changes
Compared with the contactless logical encryption card, the contactless CPU card has a separate CPU processor and chip operating system, so it can more flexibly support various application requirements and design the transaction flow more securely. At the same time, compared with the non-contact logic encryption card system, the system of contactless CPU card is more complicated, and more system modifications, such as key management, transaction process, PSAM card and card personalization, are needed.
1.1 Key Management and Authentication Mechanism
As we all know, Key Management System (KMS) is the core of IC project security. How to manage the security of the key runs through the entire life cycle of the IC card application. The secure authentication of the contactless logical encryption card relies on the independent KEYA and KEYB check of each sector. The sector control word can be used for the read/write security control of the sector data by different security combinations of KEYA and KEYB.
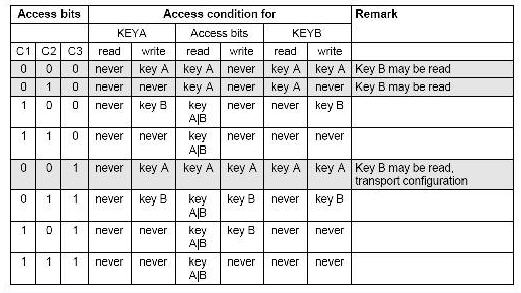
Figure 1-1 MIFARE I card sector access control
Due to the KEYA and KEYB verification mechanism, the card-to-terminal authentication can only be solved, and the terminal-to-card authentication cannot be solved, that is, the risk of the “pseudo-cardâ€, which is commonly referred to as “pseudo-cardâ€. Therefore, when a non-contact logical encryption card is used, A mechanism for card authentication codes is also used.
The non-contact CPU card can meet the security and key management requirements of different business processes with high reliability through the internal and external authentication mechanism and the transaction process of the electronic wallet defined by the Ministry of Construction. For the electronic wallet storage, the storage key can be used, the consumption can use the consumption key, the clearing can use the TAC key, the update data can use the card application maintenance key, and the card transmission key and the card owner can be used during the card personalization process. Control key, application master key, etc., truly use one key.
To implement the contactless CPU card project, you can use the key version mechanism, that is, for different batches of user cards, use different versions of keys to coexist in the system, to achieve the purpose of natural expiration of key expiration, and gradually replace the system. The key used in the system to prevent the security risks caused by long-term use of the system.
To implement the contactless CPU card project, you can also use the key indexing mechanism, that is, for the issued user card, support multiple sets of index keys at the same time. If the currently used key is leaked or there is a security risk, the system can be urgent. Activate the keys of another set of indexes without recycling and replacing the cards on the user's hand.
Therefore, in order to successfully implement the contactless CPU card project, a complete key management system is needed, which can support a variety of keys for different purposes, and supports a key version and a key indexing mechanism.
1.2 Trading Process
The transaction process of the contactless logical encryption card is relatively simple. By authenticating KEYA or KEYB, the security authority of the operation is achieved, and then the transaction operation is directly performed, and the wallet amount is increased or decreased.
Non-contact CPU card transactions are divided into inventory transactions and consumer transactions, different transaction types, with different transaction processes and security mechanisms. In the transaction of contactless CPU card, the transaction data is closely combined with the mutual authentication in the transaction process, making the transaction more secure and rigorous. At the same time, the contactless CPU card also guarantees the uniqueness and traceability of the transaction through the self-incrementing transaction serial number in the card and the transaction TAC code calculated by the card.
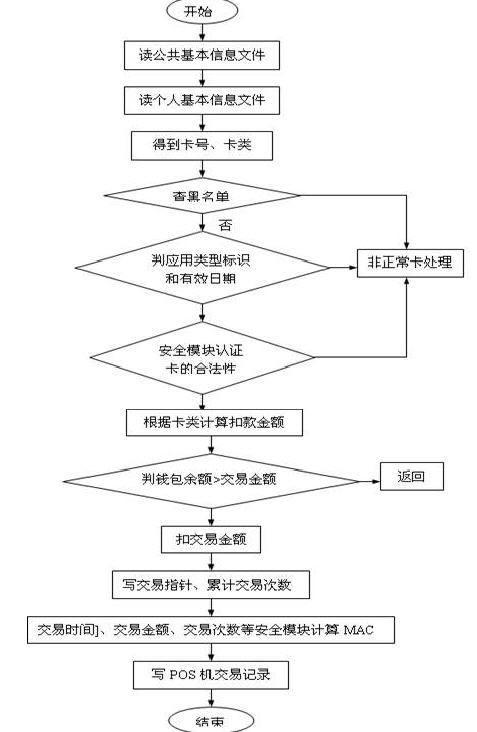
Figure 1-2 Example of a non-contact CPU card consumption transaction process
1.3 PSAM card
In the system of the contactless logical encryption card, the PSAM card mainly uses the card authentication key and the KEYA and KEYB keys of each sector to generate the KEYA and KEYB authentication codes of each sector required for the operation of the contactless logical encryption card, and the transaction Information is not directly involved in the operation.
In the non-contact CPU card system, the PSAM card is usually used to calculate and verify the MAC code appearing during the consumer transaction process. At the same time, in the process of calculation, transaction information such as transaction time, transaction amount, transaction type, etc. are also involved in the calculation, so that Trading is safer and more reliable. In some cases, the PSAM card in the contactless CPU card system can also be used to support the calculation of the MAC when the security message is updated, and the verification of the transaction TAC. Therefore, the PSAM card in the contactless CPU card system supports a wider range of functions than the contactless logical encryption card system, and is also more flexible, secure, and complex. PSAM cards that normally do not touch the CPU card system also support different key versions.
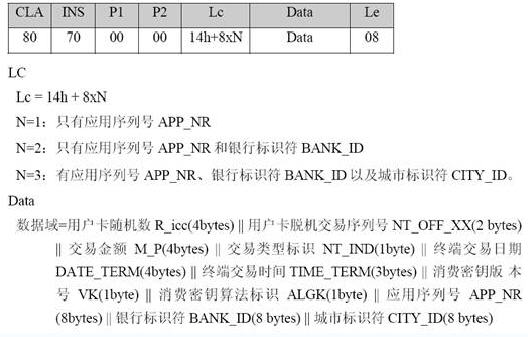
Figure 1-3 Construction Department PSAM card MAC1 calculation initialization instruction
1.4 Card personalization
The personalization of the contactless logical encryption card is relatively simple, mainly including the update of data and each sector KEYA, KEYB. During the period, all sensitive data including KEYA and KEYB are directly updated in clear text.
The personalization of non-contact CPU cards can usually be divided into two separate processes: card washing and card personalization. The former creates a card file structure, the latter updates the personalized data, and injects the corresponding key. In the process of information update and key injection, security messages are usually used to ensure the correctness and security of data and key updates. Moreover, the order of key injection and the dependency of mutual protection also fully embodies the security design of the key. For example, the card master key is usually used to protect the import application master key, and the application master key is usually used. Protect the import of other application keys, such as consumer keys.
Therefore, in order to successfully implement the contactless CPU card project, it is necessary to cooperate with the key management system to establish a safe and complete card personalization system, and equip the corresponding HSM hardware encryption machine or key mother card to realize the personalization process. Secure storage and operation of the key.
Second, matters needing attention in project implementation
In the promotion process of contactless CPU cards, some problems that require special attention and focus on solving problems have also been discovered.
2.1 Card and machine compatibility test
First and foremost is the compatibility of cards and implements. Although the ISO and many specifications have defined the electrical characteristics and data protocols between the contactless CPU card and the machine terminal, the implementation experience of many non-contact CPU card projects in China has shown that the compatibility between the card and the machine is A problem that cannot be ignored. The same machine may not be able to support cards from different card vendors; cards from the same card manufacturer may be able to trade normally on this machine and cannot be used on another machine. Even the same card, and the same machine, can succeed in one type of transaction, and fail to do another. The reason is that there are different card and machine providers with different understandings of the specifications, and some are historical technical reasons in the project implementation process.
Therefore, to successfully implement the contactless CPU card project, a large number of in-depth and comprehensive field testing is the only way to overcome the compatibility issues between cards and implements.
2.2 Multi-application extension and open platform
A very important reason for using a contactless CPU card is that the contactless CPU card can support multiple application extensions and customize different application transaction flows. In the design phase of multi-application extension, how to meet the existing specifications as much as possible, and more open to adapt to different suppliers, is an important guarantee for the long-term smooth promotion of non-contact CPU card projects. Closed systems, history has proved that they are often short-lived, unsuccessful, and cannot be widely promoted. This is the non-sufficient competition of future suppliers, and it also affects the supplier's development and investment in the corresponding products. Long-term confidence.
2.3 Trade-offs between security and transaction speed
Security and transaction speed are two common problems in non-contact CPU card projects, and they are almost a problem that every non-contact CPU card project has to face. Fast transaction speed is an important reason for adopting non-contact IC card technology. However, the one-sided pursuit of trading speed, even at the expense of security, is an inferior practice. Because there is no reliable security, it loses the meaning of adopting IC card technology, especially non-contact CPU card technology. At the same time, security often consumes a certain amount of trading time and reduces the speed of transactions. Therefore, for the contradiction between security and transaction speed, the system designer needs to balance and grasp according to the actual business needs, and find the balance between the two.
While considering security and transaction speed, especially after the optimization of transaction speed, it is especially necessary to conduct comprehensive process testing and abnormal transaction testing to ensure that transaction speed optimization will not affect the various stages of different transactions, and even create security vulnerabilities. There are many lessons in this regard.
in conclusion
Therefore, to implement the non-contact CPU card project, consider the actual needs and various factors of the system in various aspects, fully do the technical certification and planning design of the system transformation, and effectively study many technical problems in the implementation process, which is the important success of the project. Prerequisites and guarantees.
Packaging Bag,Popular Packaging Bag,Rice Packaging Bag,Plastic Packaging Bag
MST Packaging Co., Ltd. , https://www.mstpack.com